7 Fast File Transfer Software Utilities Prioritizing Speed
August 29, 2024Whether you’re sharing fun family photos or handling sensitive business data, finding a fast file transfer software is essential. But with so many options out there, how do you know which one truly delivers speed without compromising on security or ease of use?
We’ve done the homework for you! We have scoured the digital landscape to bring you the top seven fast file transfer software that are all about speed. From cloud-based solutions to specialized business tools, we’ve got something for everyone.

What Is Fast File Transfer Software
Fast file transfer software is designed to move large amounts of data quickly and efficiently. Unlike traditional methods, which can be slow and unreliable, these software solutions are optimized to handle high-speed transfers without breaking a sweat.
But what exactly makes this software "fast"? It’s all about the technology under the hood.
These tools use advanced protocols that minimize latency and maximize bandwidth utilization.
Some even offer compression features to reduce file sizes before transferring them, shaving precious seconds off your wait time. But speed isn’t the only thing that matters—security, ease of use, and compatibility are just as crucial.
The best fast file transfer software offers a balanced mix of all these elements, ensuring that you can send your files quickly without sacrificing quality or safety. Whether you’re using it for personal needs or business purposes, using in the right tool can make a world of difference.
Top 3 Fast File Transfer Software for Individual
For those who need to move files quickly without diving into complex configurations, these top three fast file transfer software options are perfect for individual users.
1. WeTransfer
WeTransfer is a SIMPLE and user-friendly online fast file transfer, that has become a go-to solution for creatives, freelancers, and businesses.
Launched in 2009, WeTransfer offers a minimalist interface that makes sending large files a breeze.
Whether you're sharing high-resolution images, video files, or important documents, WeTransfer allows you to send files up to 2GB for free.
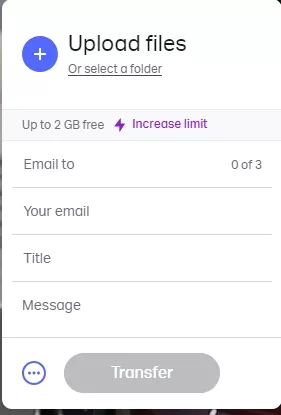
For those needing to send even larger files, WeTransfer offers a paid plan called WeTransfer Pro, which increases the file size limit to 20GB and provides additional features like password protection, customizable backgrounds, and 1TB of storage.
Pros:
- Simple and intuitive interface
- No registration required for free version
- Supports up to 2GB of file transfers for free
- Cloud-based, accessible from anywhere
Cons:
- Free version has limited features
- File size limit of 2GB may be restrictive for some users
- Paid plan required for advanced features and larger file sizes
Free Trial Policy
- WeTransfer doesn’t offer a traditional free trial since its basic service is already free for transfer up to 2GB. However, for those who need to transfer large files, they can go for a WeTransfer Pro subscription.
2. SendAnywhere
SendAnywhere is a versatile fast file transfer software that excels in providing fast, secure, and unlimited file sharing across various platforms.
One of its standout features is the ability to send files without cloud storage—files are transferred directly between devices using a 6-digit key, ensuring maximum privacy and security.
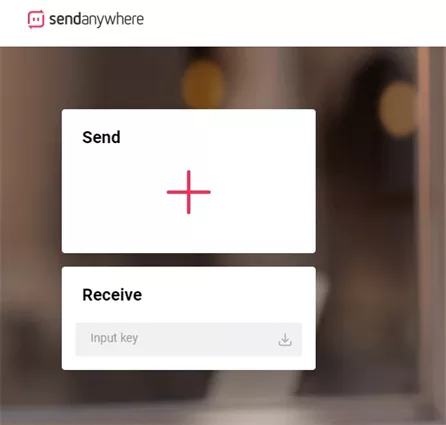
SendAnywhere supports a wide range of platforms, including Windows, macOS, Android, iOS, and Linux, making it a truly cross-platform solution.
For added convenience, SendAnywhere also offers a “link sharing” option that allows users to send files via a URL, perfect for when you need to share files with multiple recipients.
Pros:
- Unlimited file size transfers
- Cross-platform compatibility
- Direct device-to-device transfer with a secure 6-digit key
- No need for cloud storage
Cons:
- Ad-supported free version
- May require installation of an app for some features
- Some users may find the interface less intuitive
Free Trial Policy
- SendAnywhere offers a free version with all the essential features, including unlimited 1:1 real time file transfers and link creation up to 10 GB.
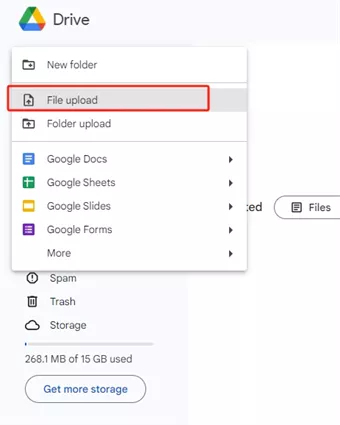
3. Google Drive
Google Drive is not just a fast file transfer software but a comprehensive cloud storage solution that integrates seamlessly with other Google services.
With Google Drive, users can store, share, and collaborate on files of all types, from documents to videos, making it an indispensable tool for both personal and professional use.
The platform supports files up to 5TB in size, provided you have the storage space available.
One of Google Drive’s strengths is its integration with Google Workspace, which includes tools like Google Docs, Sheets, and Slides. This makes it easy to share files and collaborate in real-time.
Google Drive also offers strong security features, including two-factor authentication and encryption, ensuring that your files are safe and secure during transfer.
Pros:
- Seamless integration with Google Workspace
- Real-time collaboration features
- Strong security measures
Cons:
- Free storage limited to 15GB across all Google services
- Requires a Google account
- May be overwhelming for users needing only basic file transfer
Free Trial Policy
- Google Drive offers a generous free plan with 15GB of storage. For users who need more storage and advanced features, Google Drive offers several paid plans under Google One. These plans start at 100GB and go up to 2TB.
Top 2 Fast File Transfer Software for Business [For TB-Scale Data]
When it comes to moving terabytes of data quickly, not just any file transfer software will do.
Businesses dealing with large-scale data transfers need solid solutions that can handle the heavy lifting without compromising speed or security.
Let’s look at the top 2 fast file transfer software that will help with seamless, secure and advanced file sharing.
1. Raysync
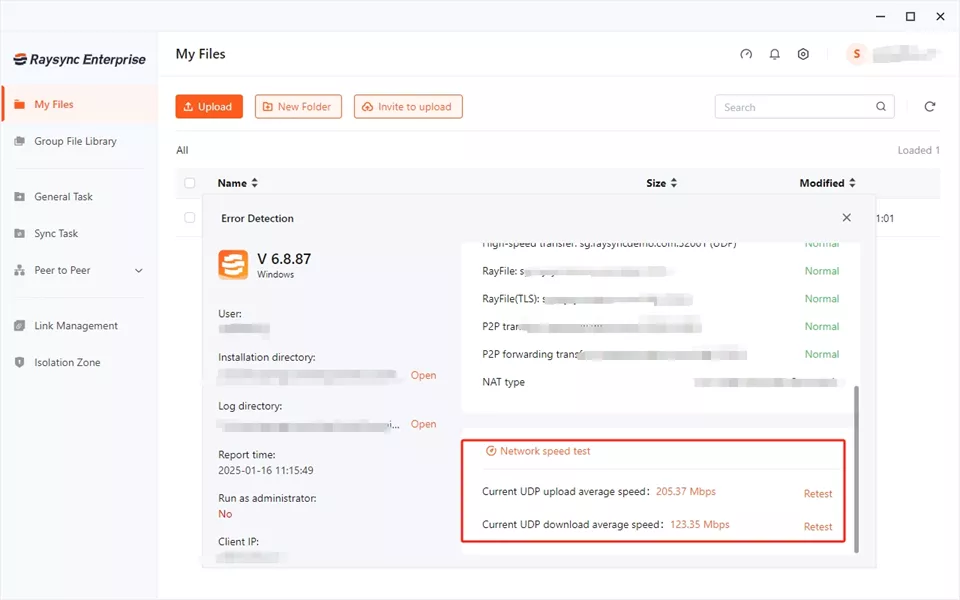
Raysync is a fast file transfer software that’s specifically designed to handle large-scale data transfers for business. With its proprietary transmission protocol, Raysync can achieve peak bandwidth utilization of up to 99%, ensuring that your data moves as quickly as possible.
It’s ideal for businesses that need to transfer terabytes of data regularly, whether for backups, media production, or global collaborations.
What sets Raysync apart is its ability to maintain speed and reliability even under challenging network conditions. It supports a wide range of transfer modes, including point-to-point, multi-point, and distributed transfers, making it incredibly versatile.
Additionally, Raysync prioritizes security with features like AES-256 encryption, SSL certificate authentication, and customizable user permissions. This makes it an excellent choice for businesses that need to move sensitive data swiftly and securely.
Pros:
- Utilizes up to 99% of available bandwidth
- Highly secure with AES-256 encryption
- Supports multiple transfer modes (point-to-point, multi-point, etc.)
- Reliable performance even in challenging network conditions
Cons:
- Primarily designed for enterprise use.
- Relatively new solution in the market.
Free Trial Policy
- Raysync offers a free trial period of 15 days, offering access to all major features, including multi-point transfers, high-speed transmission, and advanced security protocols.
2. MASV
MASV is another top-tier fast file transfer software designed for businesses that need to transfer large volumes of data.
Known for its simplicity and speed, MASV is particularly popular in the media and entertainment industries, where massive files like 4K videos and high-resolution images are the norm.
MASV is cloud-based, which means there’s no software to install, and it can be accessed from anywhere with an internet connection.
What makes MASV stand out is its pay-as-you-go pricing model, which is ideal for businesses with fluctuating data transfer needs. Instead of a flat monthly fee, you only pay for what you use, making it a cost-effective solution for businesses of all sizes.
Pros:
- Pay-as-you-go pricing model
- No software installation required
- Integrates with popular cloud storage services
- Ideal for media and entertainment industries
Cons:
- Costs can add up with frequent large transfers
- Limited to cloud-based transfers, which may not be ideal for all businesses
Free Trial Policy
- MASV provides a generous free trial with a pay-as-you-go system for those who need occasional large file transfers.
Fast File Copy Software for PC - FastCopy
FastCopy is a lightweight yet powerful fast file copy software that’s specifically optimized for speed and efficiency. Unlike traditional file copying methods built into operating systems, FastCopy leverages advanced algorithms to accelerate file transfer rates, making it an excellent tool for users who need to move large amounts of data quickly on a local PC.
One of FastCopy’s standout features is its ability to handle various file operations, including copy, move, and delete, with precision and speed. It supports a wide range of file systems, including NTFS, FAT32, and EXT4, ensuring compatibility across different storage media. FastCopy also offers multiple copy modes, allowing users to customize the process based on their specific needs.
Pros:
- Extremely fast and efficient file copying
- Supports multiple file systems
- Offers various copy modes for customization
- Lightweight and easy to use
Cons:
- Limited to local file transfers
- Interface may feel outdated to some users
- No cloud-based features
Free Trial Policy
- FastCopy is open-source fast file copy software for PC, meaning it’s completely free to use with no trial period or subscription fees.
FAQs about Fast File Transfer Software
Let’s answer some of the most common questions about fast file transfer software to help you make the best choice for your needs.
1. What is the fastest file transfer software?
When it comes to fast file transfer software, there are several contenders in the market, each with its strengths.
However, if you're looking for a solution that combines speed with reliability, Raysync is a top choice.
Its proprietary high-speed data transfer protocol allows for peak bandwidth utilization of up to 99%, making it exceptionally fast even when dealing with terabytes of data.
2. Is FTP the fastest way to transfer files?
FTP (File Transfer Protocol) is a reliable and widely used method for transferring files. However, while FTP is efficient, it may not always be the fastest option.
Factors like network conditions, file sizes, and the server’s capabilities can impact the speed of FTP transfers.
Modern alternatives like SFTP (Secure File Transfer Protocol) or specialized fast file transfer software like Raysync often provide faster, more secure, and more efficient transfer options.
3. What is the fastest way to transfer files?
The fastest way to transfer files depends on the size and type of data, as well as your specific needs.
For small to medium-sized files, cloud services like Google Drive or Dropbox can be quite efficient.
However, for large-scale data transfers, especially in a business setting, specialized software like Raysync is highly recommended.
The Bottom Line
When it comes to fast file transfer software, your choice will depend on the size of the files, the frequency of transfers, and the level of security you need. In the end, whether you’re transferring gigabytes or terabytes, picking the right software can save you both time and headaches. So, why not give Raysync a try and see how it can streamline your file transfers? Whatever you choose, make sure it fits your needs and keeps your data safe on its journey.
You might also like
![Best 8 File Backup Programs [Free/Paid]](http://images.ctfassets.net/iz0mtfla8bmk/75mGLDtGRFNt1vheyFjvaX/c6e182b3fa9d724946ed54d405ced198/file-backup-programs.png)
Industry news
October 31, 2024Secure your digital life with top-rated file backup programs. Find the perfect solution for personal and business needs.

Industry news
November 27, 2024Delve into the world of AWS File Transfer in 2025. Explore its features, pricing, and ideal use cases. Discover if it's the right solution for your file transfer needs.

Industry news
July 18, 2024Discover effective strategies for secure file sharing for business. Learn about encryption standards and best practices to protect sensitive information.