Raysync Security Design: Behavioral Audit
December 15, 2020
The large file transfer software used by enterprises will involve all aspects of enterprise data and information. Besides the security control of large file transfer software itself, the security design of enterprise user behavior is also very important. Aiming at the safety of enterprise users, Raysnc has designed strict transmission settings and user behavior control, control so as to realize visible, controllable, and traceable enterprise data flow.
1. Enterprise users
The Raysync server completely records the behavior logs of users logging in, logging out, uploading, downloading, changing passwords, sharing links, etc., and the administrator can regularly audit the user behavior information.

2. Software administrator
The Raysync server completely records the administrator's operation log, including adding, deleting, modifying user information, modifying server information, and other complete information and auditors can regularly audit the server administrator's operation behavior.

As a one-stop solution provider, Raysync has independently developed its core transfer technology with its professional technical teams to offer high-performance, secure, and reliable large file transfer and file management services for major enterprises.
You might also like
User Guide
December 11, 2020The system provides a weak password dictionary. Users can customize weak passwords that meet the password strength but are easy to be cracked by social engineering.
User Guide
November 24, 2020The recipient check "Allow to receive direct transfer files from partners" under the Point to Point option, then the Key and ID will display on the left side of the navigation bar.
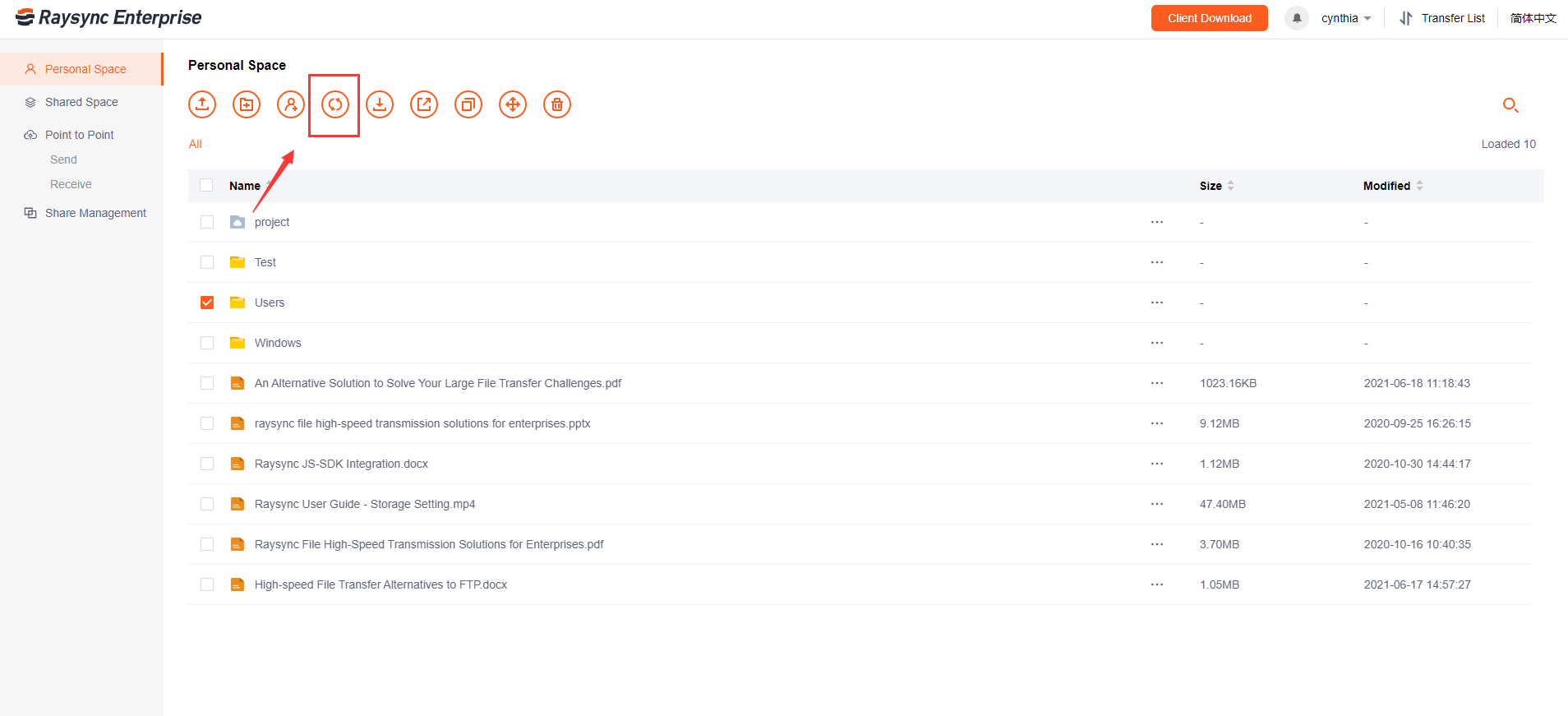
User Guide
January 27, 2021File synchronization software is used to store copies of on-premises data to another device or to the cloud. The files are typically available to be accessed via a Web-based portal.